Ways to protect your Apple devices from AirPlay attacks
Apple has always prioritized safety and user convenience in its development of new features. A prime example is AirPlay, a wireless standard developed by the company that enables users to stream audio and video between devices.
AirPlay is functional not only with Apple devices but also with televisions and speakers approved by Apple that support this wireless streaming capability. However, this makes it susceptible to attacks, and research has indicated that there are vulnerabilities in the wireless framework that could permit malicious actors to deploy malware and compromise other connected devices.
Assessing the AirPlay Risk
Security researchers at Oligo have recently revealed Airborne, a collection of security flaws in Apple’s AirPlay Protocol and the AirPlay Software Development Kit (SDK) that could enable hackers to execute code remotely. These vulnerabilities could allow malicious parties to take control of devices and exploit them to spread further harm.
“An attacker can hijack certain AirPlay-enabled devices and execute actions such as deploying malware that spreads to any local network the compromised device connects to,” Oligo stated. The potential damage is significant, considering there are billions of Apple devices that support AirPlay, along with millions from other manufacturers.
One vulnerability has the potential for hackers to infiltrate a device, subsequently gaining access to a wider network and potentially targeting additional devices. The risks vary, ranging from eavesdropping on conversations to tracking a vehicle's location, accessing confidential data, launching ransomware attacks, and causing service disruptions.
Apple has addressed these vulnerabilities through updates to macOS Sequoia 15.4, tvOS 18.4, macOS Ventura 13.7.5, iPadOS 17.7.6, macOS Sonoma 14.7.5, iOS 18.4, and iPadOS 18.4, along with visionOS 2.4 updates. Nonetheless, there are potentially thousands of older devices that will not receive these patches and remain at risk.
What Recommendations Do Experts Provide?
The primary step for safeguarding all vulnerable devices is to download the patch issued by Apple. However, this is just part of the solution. Trevor Horwitz, CISO and founder of TrustNet, mentions that the patch will only be effective if users install it after it has downloaded to their devices.
“The simplest and most effective action you can take is to keep your devices up to date. While that seems basic, it is frequently overlooked,” he states. On an iPhone or iPad, users can install the update by navigating to: Settings > General > Software Update. For macOS, you would follow this route: Apple menu > System Settings > General > Software Update.
Since vulnerabilities like Airborne leverage Wi-Fi networks to amplify their impact, users should also focus on securing those networks. Oleh Kulchytskyi, a Senior Malware Reverse Engineer at MacPaw’s Moonlock, emphasizes that Zero-Click Remote Code Execution (RCE) represents a serious security breach.
This type of vulnerability requires prompt action from the companies involved; however, as a user, additional precautions regarding your network are essential. “To remain safe at home, ensure your router has a strong password and monitor for any suspicious connections to your network,” Kulchytskyi advises.
Using AirPlay Safely
Matthias Frielingsdorf, a seasoned iOS researcher and co-founder of iVerify, suggests that everyone should adhere to fundamental digital security practices. This includes installing updates immediately upon release, using strong passwords for networks, and, most crucially, minimizing the potential attack surface.
Given that AirPlay serves as the attack vector, users should adopt proactive measures. “Disabling AirPlay on iOS, macOS, or tvOS devices that do not require it as a receiver can help limit some attacks. In public environments, turning off Wi-Fi on Mac and iPhone can also thwart these threats,” Frielingsdorf advises.
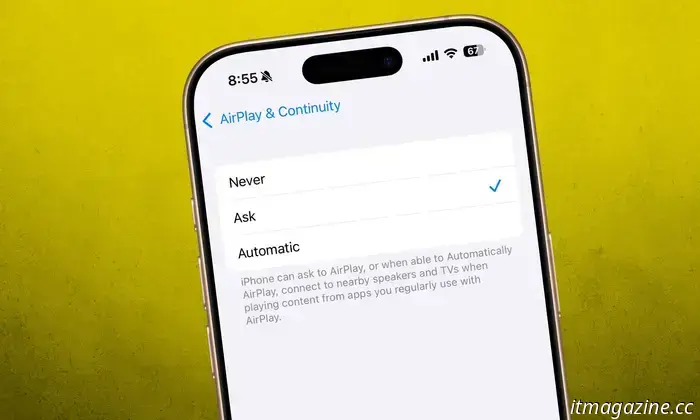
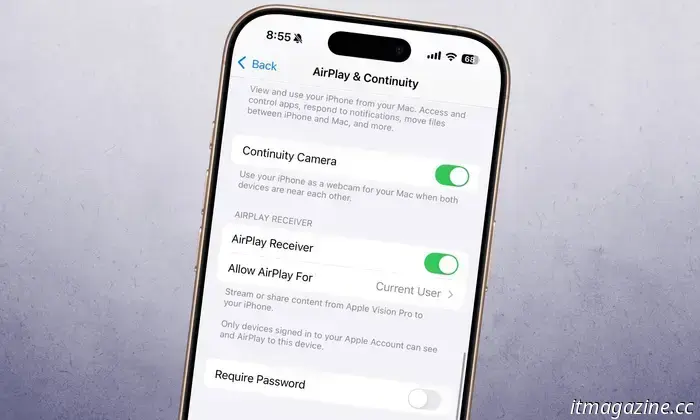
By default, AirPlay streaming is enabled, so it is crucial to disable it if not needed. To do this on an iPhone or iPad, navigate to: Settings > General > AirPlay & Continuity > Ask. Users can also select a "Never" option if they do not actively use this feature. Additionally, enabling a password for AirPlay is recommended.
Is it possible to disable AirPlay entirely? Yes, it can be fully turned off. On your iPhone and iPad, go to the AirPlay & Continuity section and toggle off the AirPlay Receiver. Alternatively, you can opt to allow AirPlay only for the Current User instead of allowing access to everyone nearby.
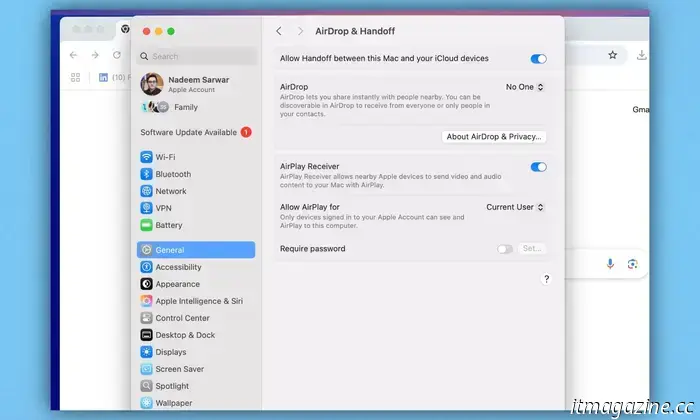
For Mac users, the path is: Apple Menu > System Settings > General > AirDrop & Handoff > AirPlay Receiver. Given that older or discontinued devices may not receive patches, it is wise to ensure that currently used devices have the appropriate settings to reduce risk.
Conclusion
Security experts have repeatedly identified weaknesses in wireless transmission protocols like Bluetooth. However, the existence of a zero-click remote code execution
Other articles
 Merriam-Webster joins the Wordle craze by launching a new daily puzzle game.
Prepare yourself for a new daily puzzle fixation brought to you by Merriam-Webster's Revealed.
Merriam-Webster joins the Wordle craze by launching a new daily puzzle game.
Prepare yourself for a new daily puzzle fixation brought to you by Merriam-Webster's Revealed.
 NYT Strands for today: clues, spangram, and solutions for Wednesday, May 21.
NYT Strands for today: clues, spangram, and solutions for Wednesday, May 21.
 Highlights from the Computex 2025 awards: The technology that wowed us most.
Computex 2025 showcased a wealth of thrilling technology, ranging from smart rings to the latest GPUs and stunning displays.
Highlights from the Computex 2025 awards: The technology that wowed us most.
Computex 2025 showcased a wealth of thrilling technology, ranging from smart rings to the latest GPUs and stunning displays.
 Get a $300 discount when you purchase the 86-inch LG QNED80 today.
The LG 86-inch QNED80 is discounted this week to $1,000, reflecting a $300 reduction from its regular price of $1,300.
Get a $300 discount when you purchase the 86-inch LG QNED80 today.
The LG 86-inch QNED80 is discounted this week to $1,000, reflecting a $300 reduction from its regular price of $1,300.
 Another esteemed Xbox exclusive is set to be released on PS5.
Players of PlayStation 5 will soon be able to immerse themselves in an atmospheric representation of Viking-age Iceland.
Another esteemed Xbox exclusive is set to be released on PS5.
Players of PlayStation 5 will soon be able to immerse themselves in an atmospheric representation of Viking-age Iceland.
 Samsung's One UI 7 is great, but adjusting this particular setting enhances its performance.
I implement an important adjustment to the notification display in One UI 7, which significantly enhances the software experience.
Samsung's One UI 7 is great, but adjusting this particular setting enhances its performance.
I implement an important adjustment to the notification display in One UI 7, which significantly enhances the software experience.
Ways to protect your Apple devices from AirPlay attacks
A recent analysis of AirPlay security has revealed that Apple's ecosystem is not invulnerable. Security experts share advice on how you can prevent becoming the next target.
